When newcomers are learning blockchain technology, they will hear about hashing and hashing algorithms, which seems to be a ubiquitous security guarantee. For example, Bitcoin or Ethereum, which runs decentralized networks and consensus machines, will have tens of thousands of nodes connected through P2P, and require "no need to be trusted" and verifiable efficiency. These systems need to write information into a compact format to ensure safety and rapid verification by participants.
The main primitive of Bitcoin and Ethereum is the noTIon of the block, which is a data structure containing transfer information, timestamps, and other important data. An important part of their security is the ability to compress all the state information of the network into very short and standard information, which can be effectively verified when needed, which is called hashing.
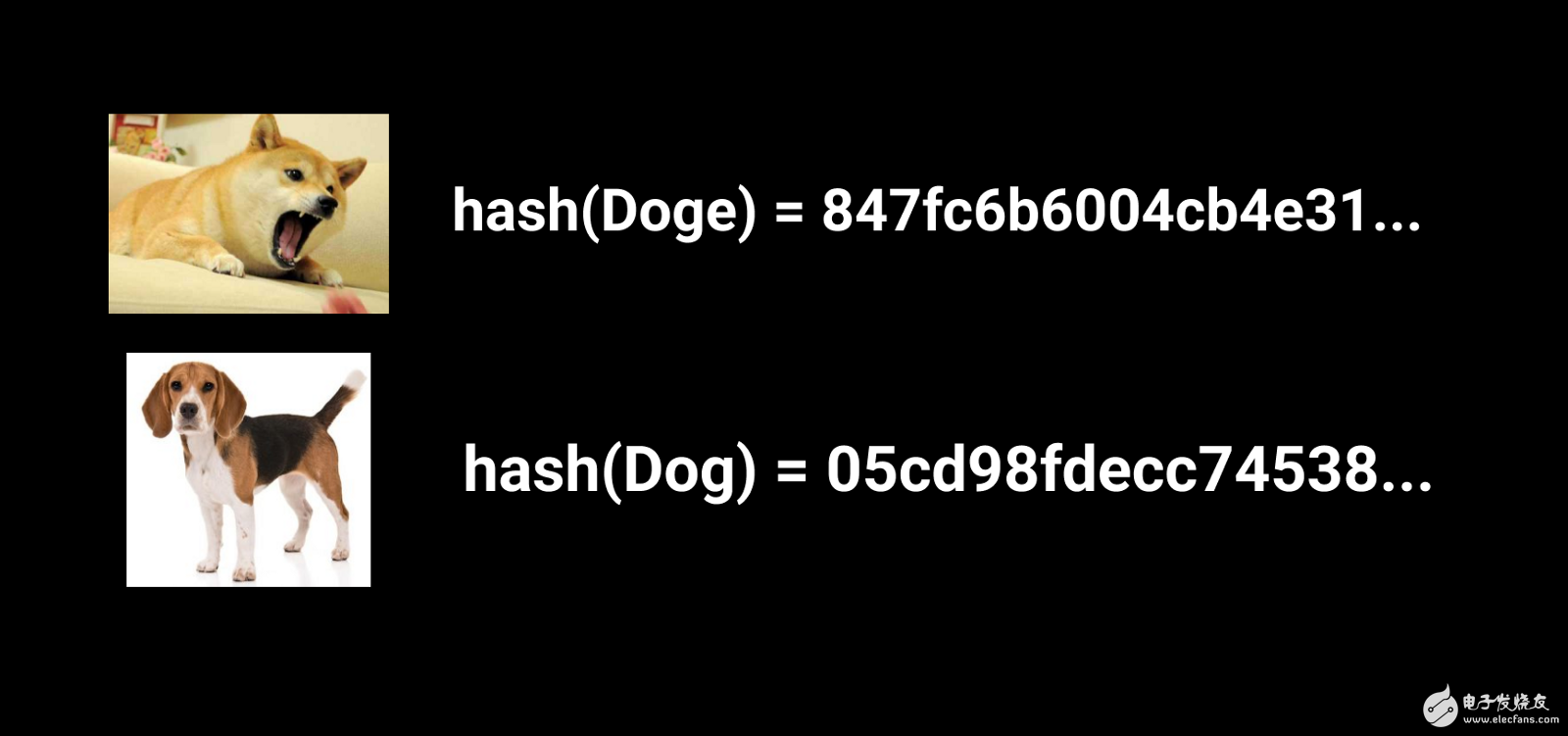
Cryptographic hashes are used everywhere, from password storage to file verification systems. The basic principle of using deterministic algorithms is to use one input and generate a fixed-length string every time. In other words, using the same input will always result in the same output.
Determinism is not only important for hashing, but a single character input can be changed to produce a completely different hash.
The problem with the hash algorithm is the inevitability of collisions. A hash is a fixed string, meaning that for each input, different inputs will produce the same output. Collisions are bad. This means that if an attacker can create such collisions on demand, he can make the fraudulent file or data look like a correct, proper hash, and impersonate it as legitimate. The goal of a high-quality hash function is to make it difficult for an attacker to find a way to get the input data.
Calculating the hash should not be too simple, because it will make it easy for an attacker to calculate collisions. The hash algorithm needs to be resistant to "pre-attack". That is, given a hash, it should be difficult to calculate the deterministic step back to regenerate the value created by the hash.
Given s= hash(x), finding x should be near impossible.
In summary, a "good" hash algorithm has the following 3 characteristics:
-Changing a character in the input should create an avalanche effect, resulting in a completely different hash
-Very low probability will produce collisions
-Improve efficiency, but will not sacrifice the confrontation of collision
Broken hash
One of the initial hash algorithm standards is MD5 hash, which is widely used for file integration verification and stores hash passwords in web application databases. This function is very simple, because the output is fixed, 128 strings for each input, and several trivial rounds of one-way operations are used to calculate its deterministic output. Its short output length and simple operation make MD5 completely fragile, which is called a birthday attack.
What is a "birthday attack"?We have heard that if you put 23 people in a room, there is a 50% probability that 2 of them will have the same birthday? Raising this number to 70 people in a room, there will be a 99.9% probability. This is what we call the pigeon nest principle, which means that if you put 100 each in 99 boxes, you must put 2 pigeons in one box. In other words, the fixed output means that the collisions may find a fixed order.

In fact, MD5's resistance to collision is very fragile, and the 2.4GHz processor used in the home can calculate the hash collision in a few seconds. Moreover, for the early use of current web pages, you can also create a lot of MD5 pre-graphics on the Internet. If you search for hashes, you can easily find them on Google.
Diversification and innovation of hashing algorithmsStart: SHA1 &SHA2
NAS is known as the pioneer of the hash algorithm standard. The original idea was the secure hash algorithm or SHA1, which created 160 fixed-length outputs. Unfortunately, SHA1 forms the MD5 algorithm by increasing the output length, the number of one-way operations, and the complexity of one-way operations, but this does not provide any basic improvement against more powerful machines. Try different attacks.
How can we do better?Enter the era of SHA3
In 2006, the National Institute of Standards and Technology proposed a competition to find an alternative to SHA2, which is nine different in nature, thus forming the standard. Therefore, SHA3 was born as part of the now known KECCAK hash algorithm.
Although it looks the same on the surface, SHA3 makes the interior very different through a mechanism called a sponge structure, which uses a random arrangement to input and output data, and also provides a random source for future input. This will enter the hash algorithm.
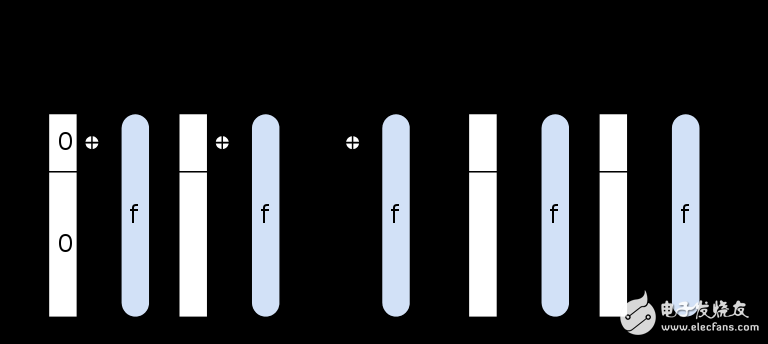
SHA3 ​​maintains the internal state and has more information related to the output, which can prevent the limitation of the previous algorithm. In 2015, it became a standard through NIST.
Hash algorithm and proof of workWhen considering the integration of the hash algorithm into the blockchain protocol, Bitcoin uses the older SHA256 algorithm, but Ethereum uses the modified SHA3 algorithm as a proof-of-work algorithm. Choosing the hash function of the proof-of-work blockchain is an important part, but the computational efficiency is called hashing.
Bitcoin SHA256 algorithm uses specific hardware ASIC to perform effective calculations. In the mining pool, many algorithms are written on ASIC, but this will also make the entire protocol develop towards centralized computing. In other words, proof of work incentivizes effective computing machines to gather into mining pools, and at the same time increases hash power. Or a machine can calculate the number of hashes in each time interval.
Ethereum uses an improved SHA3 called KECCAK256. Moreover, Ethereum's proof-of-work algorithm, Dagger-Hashimoto means that memory is difficult to calculate hardware.

Bitcoin uses the SHA256 algorithm, there will be a very interesting way to obtain hash data, because it will run 2 iterations of the algorithm in the protocol. It should be noted that this is not a countermeasure for birthday attacks, because it is obvious that if hash(x) = hash(y), then hash(hash(x)) = hash(hash(y)). However, the dual SHA256 algorithm is used to mitigate length expansion attacks.
Essentially, this type of attack involves malicious fraudsters knowing the length of the hash input, which can be used to trick the hash to start a certain part of the internal state by appending a private string to the hash value. SHA256, one of the SHA2 algorithm family, escapes this trap. Bitcoin alleviates it by calculating the hash twice.
Ethereum 2.0 and BLAKE algorithmSHA3 ​​is not the only breakthrough from the 2006 NIST Hashing Competition. Although SHA3 won, the algorithm called BLAKE took second place. For the deployment of Ethereum 2.0 sharding technology, more effective hashing is almost a feature requirement, and the research team attaches great importance to it. BLAKE2b hash algorithm, this is an updated version of BLAKE. When compared with the KECCAK256 algorithm, it is being widely used due to its high efficiency and high security.
The calculation rate of BLAKE2b is actually 3 times faster than KECCAK on modern CPUs.
The future of hashing algorithmsNo matter what we do, we can only (1) increase the complexity of the internal hash operation, or (2) increase the length of the hash output, hoping that the attacker's computer will not be fast enough to effectively calculate the collision.
We rely on the ambiguity of the image before the one-way operation of network security. In other words, the security goal of the hash algorithm is to make it as difficult as possible for everyone to find a value that can obtain the same hash output, although the value is limited for possible collisions.
Will there be quantum computers in the future? Is the hash algorithm still safe?
According to the current understanding, the answer is yes. The hash algorithm will withstand the test of quantum computers. What quantum computing can break is rigorous, the underlying mathematical structure established with clever techniques and theories, such as RSA encryption. On the other hand, the hash algorithm has less formal structure in the internal framework.
Quantum computers have indeed accelerated the speed of calculations, such as hash algorithms, but in the end, they will also be used to carry out attacks like current computers.
No matter what algorithm we choose for the protocol, it is clear that we are all in the future of efficient computing, and we must use the best way to get the right tools, and those who want to stand the test of time.
Touch Panel For Iphone,Touch Screen Digitizer Panel,Touch Screen Panel For Iphone,Phone Touch Screen
Shenzhen Xiangying touch photoelectric co., ltd. , https://www.starstp.com